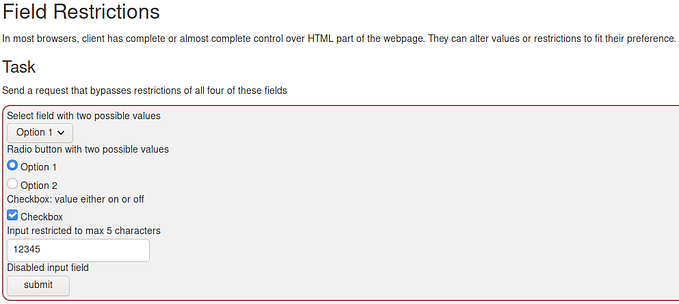
WebGoat XSS 10

This lesson is about finding routes in client-side code and understanding what is a base route

Let’s open the dev tools -> Debugger and use the almighty “find in files” functionality and search for “test” or “route”

There are many occurrences of “route” in GoatRouter.js, some of those have something to do with “test”


There is a test/:param route that calls a testHandler(param), so the parameter is passed to the lessonController

<webgoat_ip>:<webgoat_port>/WebGoat/start.mvc#test/parameterBy going to this URL, whatever is after “test/” gets reflected back to the page so the route is
start.mvc#test/WebGoat XSS 11
Starting off from what we know from XSS lesson 10, this lesson requires us to execute a JS function by injecting the payload for running webgoat.customjs.phoneHome() in the URL
So let’s copy webgoat.customjs.phoneHome() and paste it in Burp Decoder

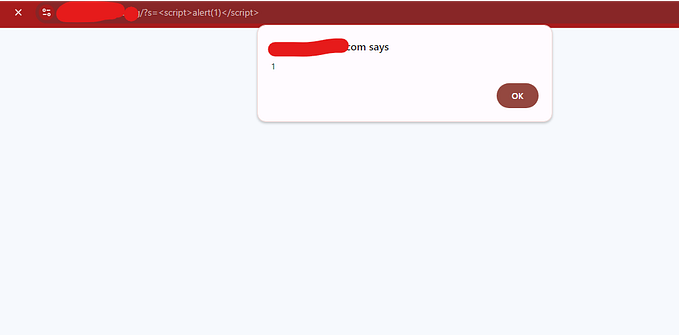
Surround it with <script> tag, URL encode it, paste it in your browser <webgoat ip>:<webgoat port>/WebGoat/start.mvc#test/ and press enter

In Burp History there should now be a response containing the random number to be used in the lesson input field
This concludes WebGoat XSS 10 11
I hope you liked it.
PVXs — https://twitter.com/pivixih